Webinars’ polling questions: How they make you a well-intentioned mole
By Mikhail Ben Rabah, CIA, CFE, CRMA
Government Audit Manager, Presidency of the Government, Tunisia.
Attending live webinars and webcasts is a common way for certified professionals to earn CPE credits and thus maintain their certifications. Hundreds of platforms provide online CPE courses. Many of these online courses are for free. If you are a CFE, CPA, CIA or other certified professional you may have attended one of these free webinars. However, they are not as gratis as they appear to be.
In most cases these webinars are sponsored by service providers and leading companies in information systems and software development, accounting solutions, ERP platforms, etc. These companies take profit from these webinars in two ways: by promoting their products related to the webinar topic and by extracting information from you.
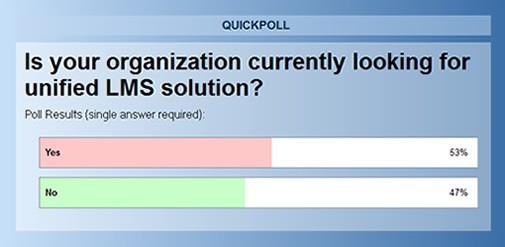
While registering for one of these free webinars, you are often required to provide information about yourself including your company’s name. To earn one CPE credit, two requirements should be generally met: attending at least 50 minutes of the webinar and answering poll questions that appear at regular time intervals on your screen. Here’s the clue: the questions they may ask you are not designed to test your knowledge or what you have learned about the topic addressed.
Surprisingly, poll questions aim to gather information about your organization/business: maturity of your governance, risk management, IT processes, major concerns, future projects and so on. If this information is gathered for wide industry surveys like the ones conducted by professional associations or international organizations, there would not be an issue with that. This kind of surveys are legitimate and based on agreed-upon terms with regard to information confidentiality and purpose use.
However, information gathered through webinars’ polling question may be used for the sponsor’s business and commercial goals. Personally, I’ve been seeing many questions about sensitive data like type of employee conflicts handled by organizations, fraud schemes discovered, potential liabilities, etc. This could be considered as a smooth and creative corporate espionage although it does not expose the sponsor to any liability since you have intentionally provide the answers. Do not forget that people are the biggest vulnerability of information security. Individuals and companies will not stop inventing genius techniques and tools to extract information from you.
Hence, they may have made you, without knowing, a well-intentioned insider. Certainly, no one from your organization will know about information you have provided but if you are ethically uncomfortable with that, start by checking if your organization’s information security policy addresses similar issues. Otherwise, if you still feel wrongdoing and betraying your organization, here is a tip: for your company’s name, just provide a fake one.
- Shall internal auditors be prepared to “Metaverse”? - November 6, 2021
- Overzealousness, a Threat to Auditors’ Objectivity? - January 19, 2021
- How Worthy Time Management is in Internal Auditing - December 28, 2020

Stay connected